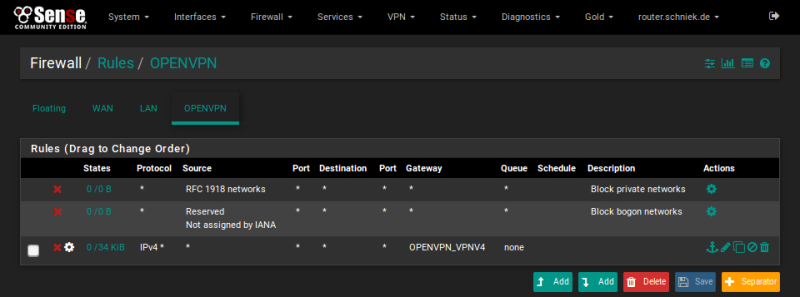
Step 1
Open [Certificate Manager] in menu [System]
In tab [CAs] click [Add] button
Enter PrivateVPN as [Descriptive name]
Enter this in [Certificate data] field and click [Save] button
—–BEGIN CERTIFICATE—–
MIIErTCCA5WgAwIBAgIJAPp3HmtYGCIOMA0GCSqGSIb3DQEBCwUAMIGVMQswCQYD
VQQGEwJTRTELMAkGA1UECBMCQ0ExEjAQBgNVBAcTCVN0b2NraG9sbTETMBEGA1UE
ChMKUHJpdmF0ZVZQTjEWMBQGA1UEAxMNUHJpdmF0ZVZQTiBDQTETMBEGA1UEKRMK
UHJpdmF0ZVZQTjEjMCEGCSqGSIb3DQEJARYUc3VwcG9ydEBwcml2YXR2cG4uc2Uw
HhcNMTcwNTI0MjAxNTM3WhcNMjcwNTIyMjAxNTM3WjCBlTELMAkGA1UEBhMCU0Ux
CzAJBgNVBAgTAkNBMRIwEAYDVQQHEwlTdG9ja2hvbG0xEzARBgNVBAoTClByaXZh
dGVWUE4xFjAUBgNVBAMTDVByaXZhdGVWUE4gQ0ExEzARBgNVBCkTClByaXZhdGVW
UE4xIzAhBgkqhkiG9w0BCQEWFHN1cHBvcnRAcHJpdmF0dnBuLnNlMIIBIjANBgkq
hkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwjqTWbKk85WN8nd1TaBgBnBHceQWosp8
mMHr4xWMTLagWRcq2Modfy7RPnBo9kyn5j/ZZwL/21gLWJbxidurGyZZdEV9Wb5K
Ql3DUNxa19kwAbkkEchdES61e99MjmQlWq4vGPXAHjEuDxOZ906AXglCyAvQoXcY
W0mNm9yybWllVp1aBrCaZQrNYr7eoFvolqJXdQQ3FFsTBCYa5bHJcKQLBfsiqdJ/
BAxhNkQtcmWNSgLy16qoxQpCsxNCxAcYnasuL4rwOP+RazBkJTPXA/2neCJC5rt+
sXR9CSfiXdJGwMpYso5m31ZEd7JL2+is0FeAZ6ETrKMnEZMsTpTkdwIDAQABo4H9
MIH6MB0GA1UdDgQWBBRCkBlC94zCY6VNncMnK36JxT7bazCBygYDVR0jBIHCMIG/
gBRCkBlC94zCY6VNncMnK36JxT7ba6GBm6SBmDCBlTELMAkGA1UEBhMCU0UxCzAJ
BgNVBAgTAkNBMRIwEAYDVQQHEwlTdG9ja2hvbG0xEzARBgNVBAoTClByaXZhdGVW
UE4xFjAUBgNVBAMTDVByaXZhdGVWUE4gQ0ExEzARBgNVBCkTClByaXZhdGVWUE4x
IzAhBgkqhkiG9w0BCQEWFHN1cHBvcnRAcHJpdmF0dnBuLnNlggkA+ncea1gYIg4w
DAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAQEAayugvExKDHar7t1zyYn9
9Vt1NMf46J8x4Dt9TNjBml5mR9nKvWmreMUuuOhLaO8Da466KGdXeDFNLcBYZd/J
2iTawE6/3fmrML9H2sa+k/+E4uU5nQ84ZGOwCinCkMalVjM8EZ0/H2RZvLAVUnvP
uUz2JfJhmiRkbeE75fVuqpAm9qdE+/7lg3oICYzxa6BJPxT+Imdjy3Q/FWdsXqX6
aallhohPAZlMZgZL4eXECnV8rAfzyjOJggkMDZQt3Flc0Y4iDMfzrEhSOWMkNFBF
wjK0F/dnhsX+fPX6GGRpUZgZcCt/hWvypqc05/SnrdKM/vV/jV/yZe0NVzY7S8Ur
5g==
—–END CERTIFICATE—–
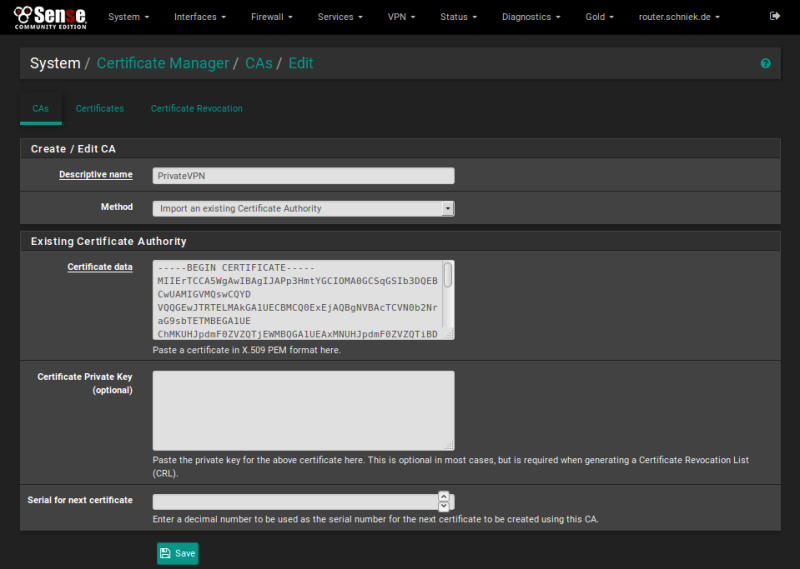
Step 2
Open [OpenVPN] from [VPN] menu, switch to tab [Clients] and click [Add] button
Fill in the data for:
Server mode: Select [Peer to Peer ( SSL/TLS )]
Protocol: UDP
Device mode: tun
Server host or address: You’ll find the server list here: Server list
Server port: 1194
Proxy Auth. – Extra options: none
Description: Name of the country, city and server address
Username: Enter your email address for PrivateVPN
Password: Enter your PrivateVPN password
TLS authentication: Enable
Key:
—–BEGIN OpenVPN Static key V1—–
f035a3acaeffb5aedb5bc920bca26ca7
ac701da88249008e03563eba6af6d262
5ac8ba1e5e0921f76be004c24ae4fd43
e42caf0f84269ad44d8d4c14ba45b138
6f251c7330d8cc56afd16d5168356456
51ef7e87a723ac78ae0d49da5b2f2d78
ceafcff7a6367d0712628a6547e5fc8f
ef93c87f7bcd6107c7b1ae68396e944a
adae50111d01a5d0c67223d667bdbf1b
f434bdef03644ecc5386e102724eef38
72f66547eb66dc0fea8286069cb082a4
1c89083b28fe9f4cec25d48017f26c4f
d85b25ddf2ae5448dd2bccf3eef2aacf
42ef1e88c3248c689423d0b05a641e9e
79dd6b9b5c40f0cc21ffdc891b9eee95
1477b537261cb56a958a4f490d961ecb
—–END OpenVPN Static key V1—–
Peer Certificate Authority: Select [PrivateVPN]
Client Certificate: Select [None (Username and/or Password required)]
Encryption Algorithm: Select [AES-256-CBC (256 bit key, 128 bit block)]
Auth digest algorithm: Select [SHA256 (256-bit)]
Hardware Crypto: If your device do not support hardware crypto please select [No Hardware Crypto Acceleration]
Compression: Select [Enable with Adaptive Compression]
Topology: Select [Subnet – One IP address per client in a common subnet]
Custom options:
remote-cert-tls server;
client;
comp-lzo;
persist-key;
persist-tun;
auth-nocache;
connection retry -1;
route-delay;
keepalive 3 10;
Click [Save] button
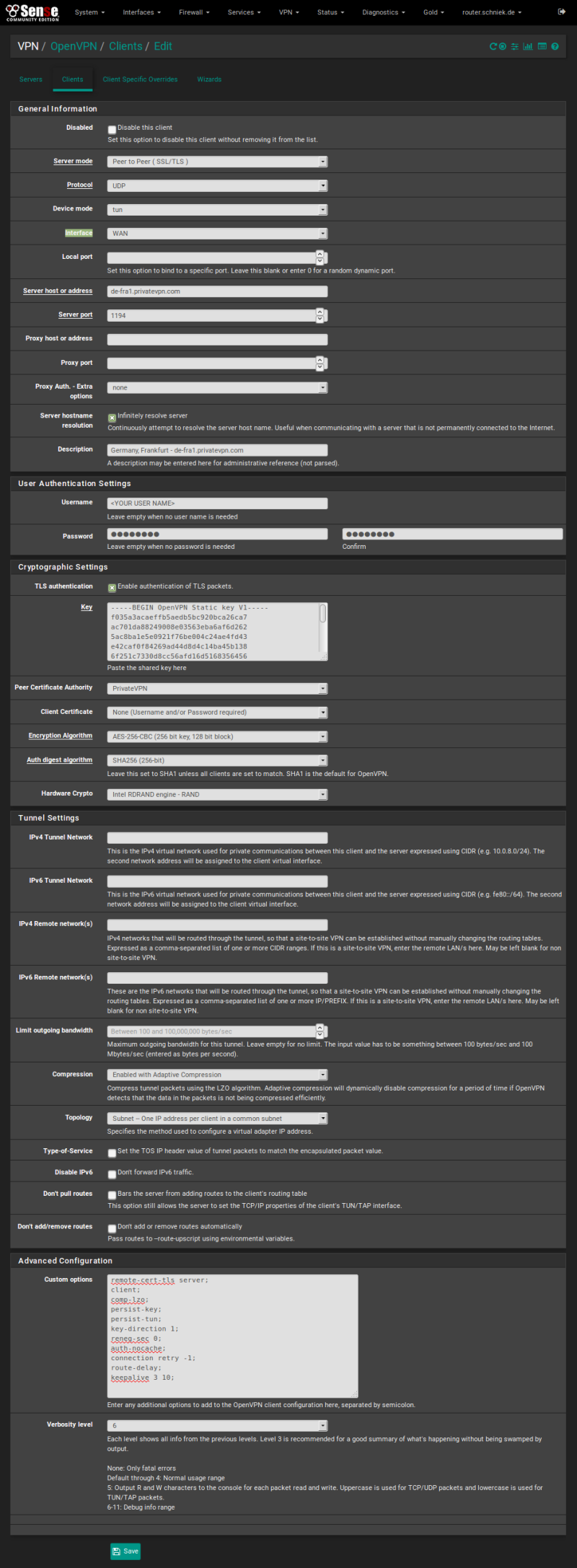
Step 3
Open (Interface Assignments) from [Interfaces] menu and select the newly created tunnel [ovpn1 (Germany, Frankfurt – de-fra1.privatevpn.com)] from dropdown menu
Step 4
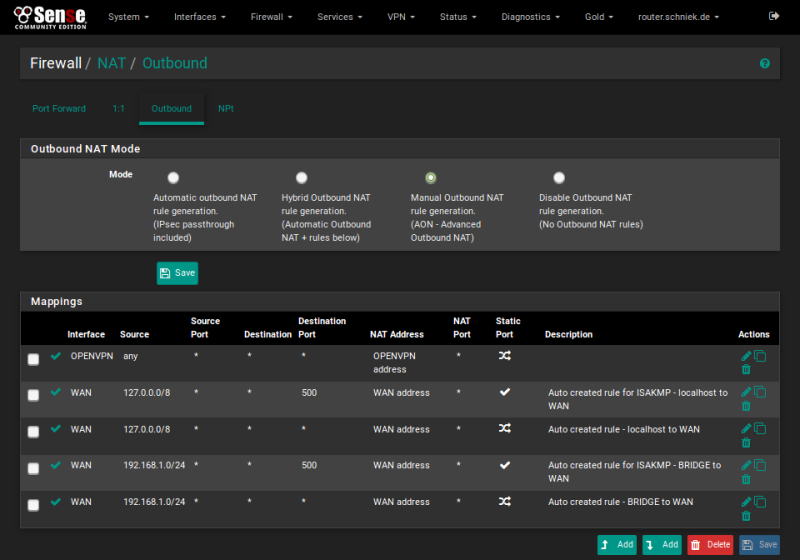
Open [NAT] from [Firewall] menu and switch to tab [Outbound]
Change to manual and duplicate outbound rules for VPN like this:
Step 5
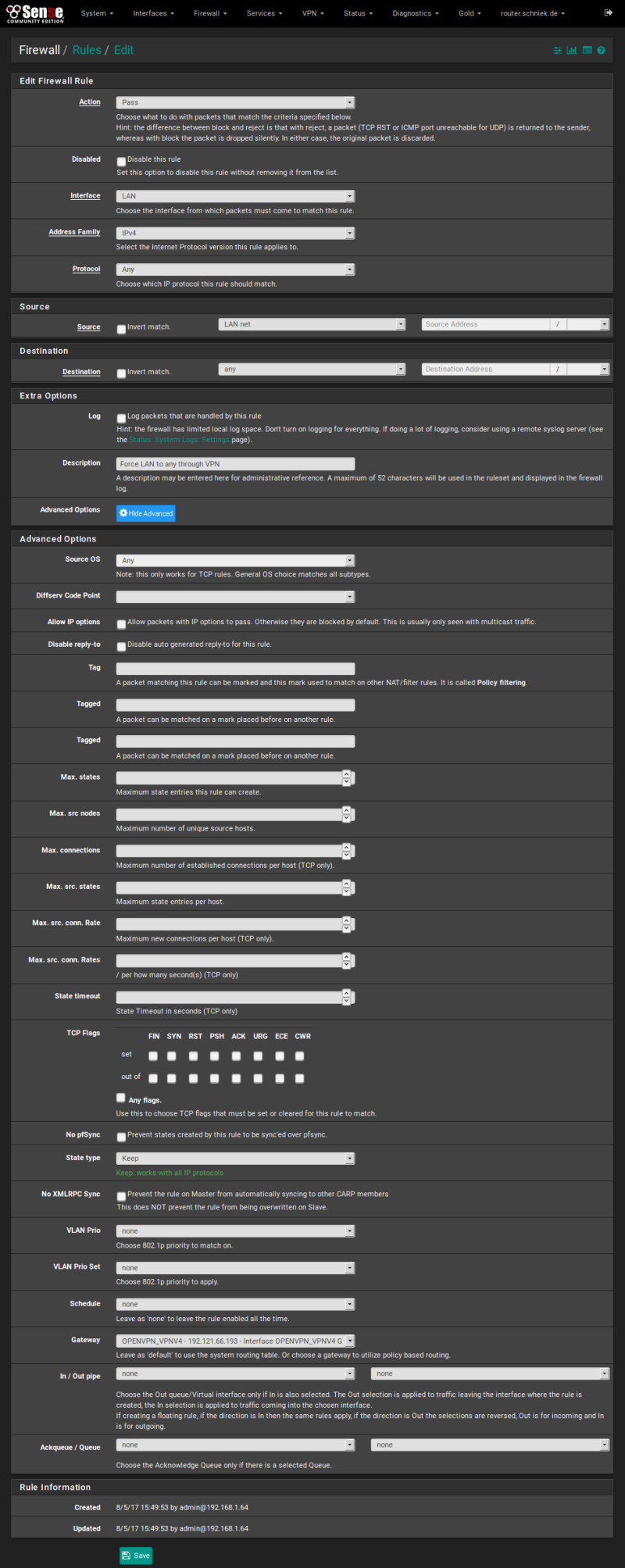
Open [Rules] from [Firewall] menu and switch to tab [LAN]
Copy default LAN to any rule like this: (note Advanced Gateway Setting)
Step 6
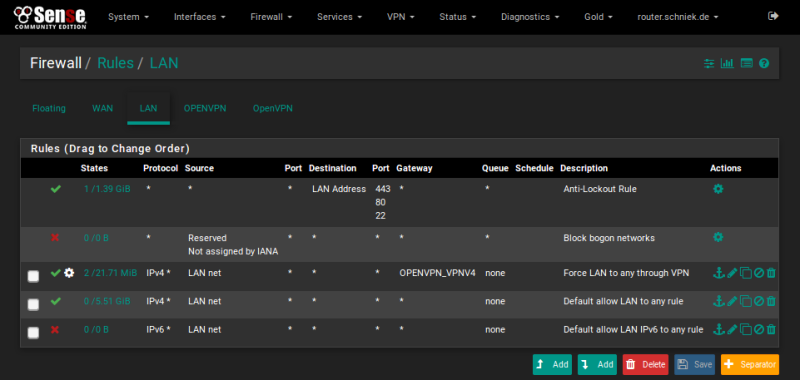
Should look like this when saved: Default rules can be disabled or removed if wanted.
Step 7
Create Allow any rules on interfaces PrivatVPN and OpenVPN